3.1- Intent Interpretation and Network Observation
Network monitoring typically involves defining multiple tasks and deploying mechanisms to measure latency, loss, and availability metrics. These mechanisms require careful planning and must be consistently executed across devices. Collected data must then be exported to a central interface, where it can be interpreted in the context of service performance. This process is often complex and resource-intensive.
In this test, we evaluated NCE-FabricInsight's ability to simplify and automate that workflow by processing high-level monitoring intents and translating them into executable monitoring tasks.
NCE-FabricInsight supports two levels of monitoring. The first is Data Plane Verification (DPV), which checks device configurations and operational state using collected configuration files and gNMI telemetry.
The second level is Assurance Service Monitoring, where traffic performance is observed in real time. This is achieved using port mirroring and Encapsulated Remote Switch Port Analyzer (ERSPAN). Port mirroring is typically configured on border leaf switches, where selected traffic is mirrored to a probe server for analysis. ERSPAN forwards the mirrored traffic—often limited to TCP headers—over GRE tunnels, allowing the probe server to reconstruct TCP flows, track sequence numbers, and detect issues such as retransmissions or connection setup failures.
Additionally, NCE-FabricInsight supports In-situ Flow Information Telemetry (IFIT) for direct measurement of network path performance. IFIT inserts telemetry metadata into live data packets, enabling hop-by-hop tracking of delay, jitter, and packet loss without requiring active test traffic.
To test the platform's intent processing, we defined a monitoring intent for a selected IP address pair in security zones 3 and 4 as shown in Figure 26 below.
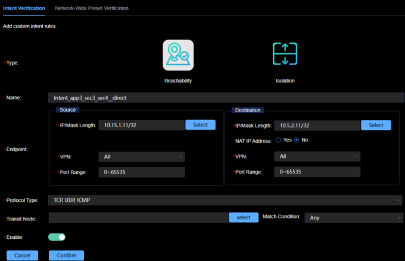
Figure 26: Monitoring Intent
NCE-Fabric processed the defined intent and analyzed all available paths between the selected endpoints. A total of 16 paths were identified, each going through different spine and border leaf node combinations. All paths were marked as reachable, indicating no connectivity issues between the defined IP addresses.
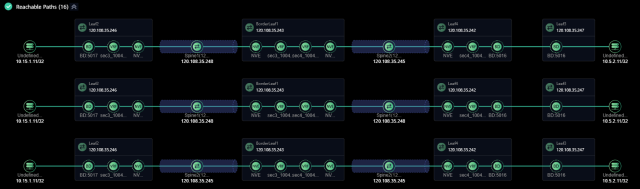
Figure 27: Reachability Status Between the Defined Endpoint
We then extended the intent by creating an assured application based on the defined IP pair. This activated SLA monitoring, allowing us to define thresholds for metrics such as connection success rate, latency, and setup time. In addition to these, NCE-FabricInsight supports detailed health monitoring across multiple categories, including Connection Setup, Congestion Control, Packet Loss, Retransmission, Delay, Throughput, Payload, and Concurrency, each with various parameters and configurable thresholds, as shown in Figure 28.
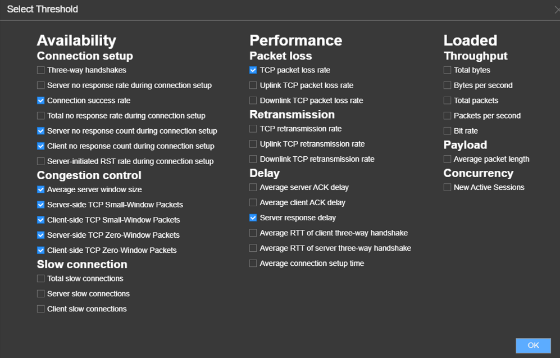
Figure 28: SLA Threshold Configuration Options
In addition to the previously defined IPv4 monitoring intent between two IP addresses in the security zones 3 and 4, we created a second intent using an IPv6 address pair for the same security zones. Both intents were processed similarly, with NCE-FabricInsight enabling path analysis and SLA monitoring for each flow. Figure 29 illustrates the exact path taken by traffic associated with the monitored IPv6 addresses, including the intermediate hops. The traffic was forwarded from the spine to the border leaf and then back to the spine. This reflects the expected behavior for inter-security zone communication, as this type of traffic typically passes through the border leaf.
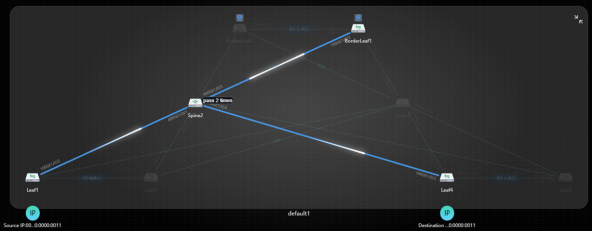
Figure 29: Traffic Path of the Monitored IPv6 Addresses Pair
It is worth noting that the association between applications and the IP addresses to be monitored must be defined manually. Automatic detection of application-level flows is only supported when a load balancer is present in the network design. Additionally, port mirroring is configured by default only for IPv4 traffic and does not include IPv6. Manual port mirroring must be configured to enable end-to-end path visibility and route condition analysis for the previously created IPv6-based intent. This mirroring still uses the existing IPv4 GRE tunnel, so no additional tunnel setup is required. However, enabling IPv6 monitoring does require additional ACL entries to cover mirrored traffic types, including VXLAN, IPv4, and IPv6.
This test verified that NCE-FabricInsight automatically translated the defined intent into concrete monitoring tasks. It also generated SLA tracking for metrics such as latency, connection setup success rate, and retransmissions and activated a range of health indicators, each with configurable thresholds. Although IPv6 monitoring required manual configuration, including port mirroring and ACL setup, this did not affect the platform's ability to perform the monitoring tasks. These observations confirm that NCE-FabricInsight supports the Scenario-Based Monitoring capability as defined in the ETSI GR ENI 049 specification.
| < Previous | Next > |
